4 Minutes
Samsung has issued an urgent alert after a critical software vulnerability—tracked as CVE-2025-21043—was found to be exploited in the wild. The flaw affects Galaxy devices running Android 13 and later, including recent flagships such as the Galaxy S25 and Galaxy S25 Edge. Samsung’s September security update includes a patch to address the issue; users are strongly advised to install it as soon as their device receives the rollout.
What went wrong
Technical details
The vulnerability resides in a closed-source image parsing library developed by Quramsoft and can result in an out-of-bounds write. In practice, a remote attacker can deliver a specially crafted image file that, when processed by a vulnerable device, writes overflow data into memory. If that data lands in a precise location, it can be executed—allowing the attacker to gain control of the phone. WhatsApp reported the flaw, but it’s currently unclear whether other messaging platforms are affected.
Because the exploit can be triggered without user interaction (a zero-click attack), victims do not need to open a message or tap a link for the compromise to occur. That stealth makes it far more dangerous than conventional phishing or social engineering attacks.
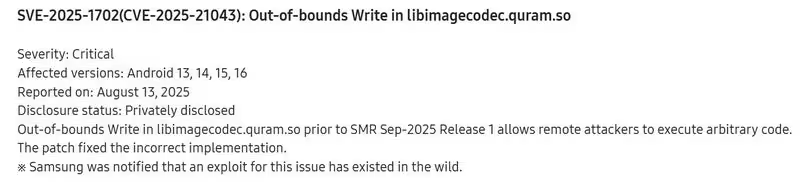
The vulnerability listed in Samsung's monthly security report. | Image credit-Samsung
Who is most at risk
Zero-click exploits are complex and often associated with targeted espionage. Historically, such attacks have been used against high-profile individuals—journalists, diplomats, politicians and defense personnel—by well-funded actors. Nevertheless, unpatched devices owned by anyone can be targeted, so installing updates matters for all users.
How to protect your Galaxy
Immediate steps
- Install Samsung’s September security patch as soon as it becomes available for your model and carrier.
- Keep Android system updates and all apps up to date—messaging apps in particular.
- Enable automatic updates where possible and avoid installing apps from untrusted sources.
- Consider additional protections such as Google Play Protect and Samsung Knox features for enterprise devices.
Product features, comparisons and advantages
Samsung’s monthly security bulletin and staged update model (by device model, country and carrier) give enterprises and consumers predictable patch cycles, but they also mean some devices receive fixes later than others. Compared with Apple’s more centralized rollouts or Google’s Pixel update cadence, Galaxy updates can be staggered—so checking for updates regularly is essential.
Samsung devices benefit from built-in security layers like Knox and regular security releases. Still, the presence of a closed-source third-party library highlights supply-chain risks that affect devices across manufacturers. Recent similar zero-click issues reported by WhatsApp on iPhone further underline that messaging platforms and image parsers are a frequent attack surface.
Use cases and market relevance
For enterprises, government agencies and high-risk users, this vulnerability reinforces the need for rapid patch management and mobile threat defense solutions. For general consumers, the episode is a reminder to prioritize OS and app updates: protecting personal data, banking apps and two-factor authentication tokens depends on timely security maintenance.
Bottom line
Although these exploits are rare and often targeted, they are severe. If you own a Galaxy device running Android 13 or newer, check for the latest Samsung system and security updates now and keep your messaging apps current. Prompt installation of the fix is the simplest and most effective defense against CVE-2025-21043.
Source: phonearena


Leave a Comment