5 Minutes
Binance founder alerted to potential government-backed breach
Changpeng Zhao, better known as CZ, shared a Google security alert that flagged a possible attempt by "government backed hacking attackers" to access one of his accounts. The former Binance CEO posted the warning on X, prompting discussion across crypto and cybersecurity circles about the growing threat of state‑sponsored hacking groups targeting high‑profile figures and crypto infrastructure.
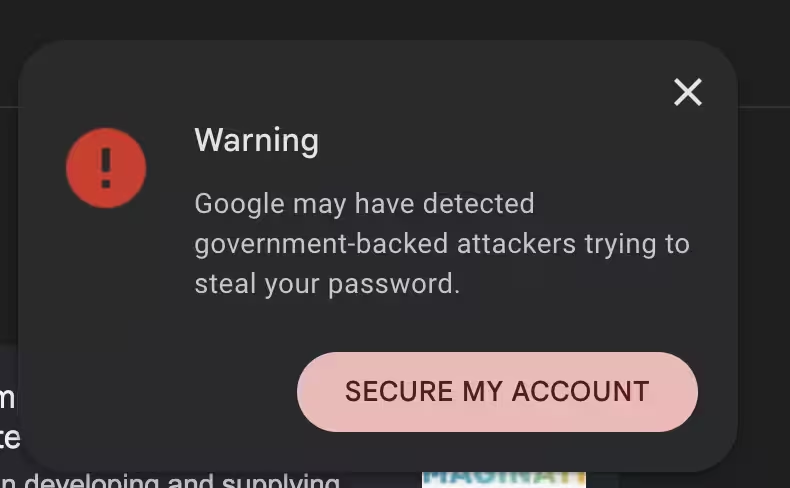
Google warning about account security
What the alert means and Google’s clarification
Google has long issued alerts when it detects signs that a "government-backed" actor may have tried to target an account. According to Google’s own guidance, these notices are precautionary and do not necessarily confirm that an account has been compromised. The company explains that such warnings reflect intelligence that a government‑linked attacker likely made an attempt — often via phishing, malware, or other advanced intrusion techniques — but they are not proof of a successful breach.
CZ’s response and public reaction
Zhao downplayed the alarm, noting he doesn’t store anything important on the flagged account and encouraging followers to practice good security hygiene. Still, his post highlighted how public figures in crypto — with large followings and deep industry connections — remain attractive targets for state‑sponsored threat actors aiming to infiltrate exchanges, wallets, or venture operations.
Lazarus group: a persistent threat to crypto
In his public comments, CZ speculated that North Korea’s Lazarus group could be behind the attempted access. Lazarus is one of the most notorious state‑backed hacking collectives accused of carrying out a string of high‑profile crypto heists and wallet infrastructure attacks. Security firms and blockchain forensic teams have repeatedly tied Lazarus to multi‑million dollar thefts, alleging the group uses complex social engineering, supply‑chain intrusion, and malware campaigns to drain funds from exchanges and institutional wallets.
Past attacks and industry impact
Notable incidents attributed to Lazarus include attacks on exchanges and crypto platforms that resulted in significant asset losses. These operations often rely on impersonating IT personnel or exploiting insider access to bypass security controls. Estimates from blockchain analytics companies suggest funds stolen by state‑sponsored hacking groups may represent a sizable share of revenue for sanctioned regimes, underlining the geopolitical motive behind many crypto attacks.

Why high‑profile crypto leaders are targeted
CZ’s visibility — his influence over projects, mentorship of startups, and leadership of venture initiatives — makes him a high‑value target. Attackers aiming to access sensitive communications, private keys, or privileged connections can achieve outsized results from compromising a single executive or developer account. The risk extends beyond direct financial theft to reputational damage, insider information leaks, and coordinated social engineering campaigns that exploit trust networks within the crypto ecosystem.
Practical security steps for crypto professionals
Whether you’re an exchange operator, developer, or investor, the following measures reduce exposure to state‑level threats: enable hardware-backed multi‑factor authentication, use isolated devices for key management, apply endpoint protection and regular patching, vet third‑party vendors carefully, and train teams to recognize sophisticated phishing and supply‑chain attacks. Regularly reviewing access logs and adopting zero‑trust principles can also limit damage if an intrusion occurs.
Looking ahead: surveillance, sanctions and the crypto landscape
The incident serves as a reminder that the intersection of geopolitics and cryptocurrency creates persistent cybersecurity risks. As nation‑state actors increasingly target blockchain infrastructure and prominent industry figures, exchanges, custodians, and projects must continue investing in threat intelligence, forensic capabilities, and layered defenses. Meanwhile, public warnings from tech firms like Google help raise awareness, but they also highlight the need for decisive, proactive security practices across the entire crypto sector.
For industry participants and users alike, the takeaway is clear: treat government‑linked security alerts seriously, but follow verified guidance from platform providers, secure accounts proactively, and maintain an assumption that sophisticated adversaries will continue to probe crypto systems worldwide.
Source: crypto


Leave a Comment