8 Minutes
Social engineering cost crypto billions in 2025
2025 proved to be a watershed year for crypto security: attackers shifted focus from exploiting software bugs to manipulating people. Advances in artificial intelligence have made social-engineering campaigns more convincing than ever, and security experts warn that many of next year’s losses will be driven by human error rather than broken code. This article explains how those attacks played out this year and lays out practical defenses for both individuals and organizations in the blockchain ecosystem.
The scale of the losses and how they happened
From January through early December 2025, Chainalysis data shows more than $3.4 billion was stolen from blockchain projects, exchanges, and users. One high-profile incident—the February compromise of a major exchange—accounted for nearly half that total. In that attack, adversaries gained entry through targeted social engineering, injected a malicious JavaScript payload, altered transaction parameters and siphoned funds.
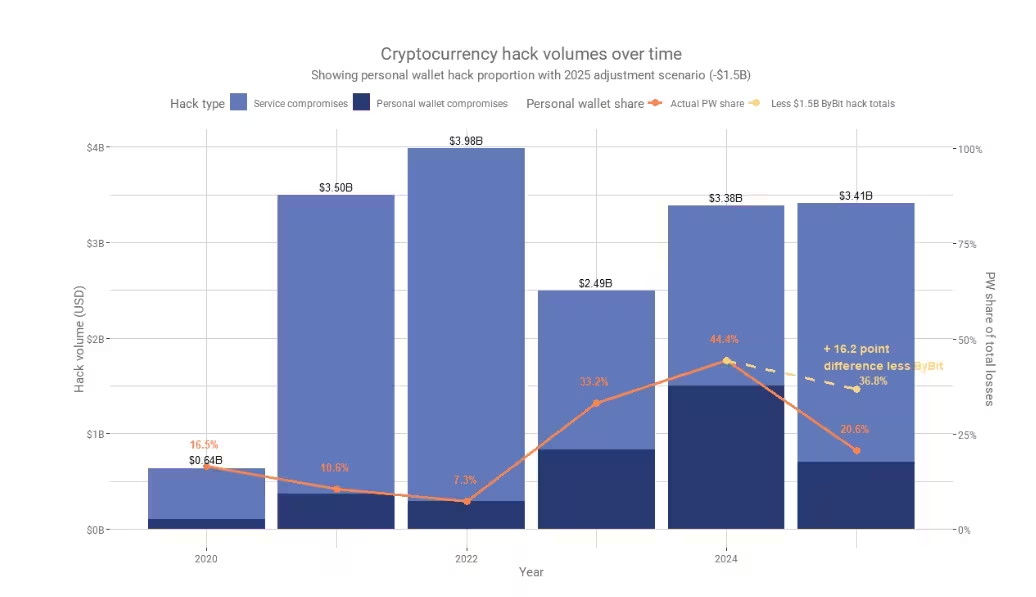
Over $3.4 billion was stolen by bad actors this year
What is social engineering in crypto?
Social engineering is a class of cyberattacks that relies on psychological manipulation to make victims reveal sensitive information, disclose credentials, or perform actions that undermine security. In the context of crypto and blockchain, social engineering can lead to leaked wallet keys, compromised signing tokens, poisoned software updates, and unauthorized transactions.
Why people are the primary target
Security leaders now argue that the battlefield has shifted from purely technical defenses to human awareness. Attackers are increasingly focused on creating credible interactions — convincing phone calls, tailored emails, convincing deepfake video calls, or fraudulent developer recruitment exercises — to trick people into granting access. Rather than breaking into systems, many incidents begin with a conversation that lowers suspicion and opens a door.
Tip 1: Automate defenses and reduce human trust points
Supply chain compromises and cloud credential leaks this year showed how a single lapse can cascade into a major incident. Because modern systems resemble a digital Jenga tower, every dependency and integration matters. Security professionals recommend moving from reactive responses to preventive automation wherever feasible.
Practical automation and verification steps
- Automate authentication and authorization flows so human approval is limited to exceptional, verified cases.
- Use automated signing policies and multi-signature gating for critical transactions to prevent unilateral approvals.
- Deploy AI-driven anomaly detection to flag abnormal behaviors, such as unusual signing patterns or non-standard API calls, before funds move.
Smarter identity verification and AI-based threat detection can spot suspicious activity faster than manual monitoring, but no automation replaces disciplined user behavior.
Tip 2: Silo infrastructure and harden developer workflows
Attackers increasingly targeted developer ecosystems, using leaked cloud credentials and poisoned packages to insert malicious code and alter deployment pipelines. To mitigate these risks, teams must limit blast radiuses through environment separation and strict package validation.
Developer best practices
- Pin dependency versions and verify package integrity before use.
- Isolate build and CI/CD environments from production systems and secrets.
- Require code reviews and cryptographic signing for all releases and updates.
Security teams should implement strong access controls, periodic key rotation, hardware-backed authentication, and continuous monitoring to detect credential theft. For individuals, rely on hardware wallets, avoid opening unverified files or links, and confirm identities through independent channels before responding to requests.
Tip 3: Counter AI deepfakes with proof of personhood
AI-generated deepfakes and tailored social attacks emerged as a major concern in 2025. Attackers have used synthetic voices and video to impersonate founders, partners, or employees in live calls or recorded messages to extract secrets. These are not hypothetical risks — teams have already reported attempts to use fake Zoom calls to trick insiders into revealing sensitive data.
Technical steps to defend against AI-enabled impersonation
- Introduce cryptographic proof-of-personhood for critical communications so identities can be verified via signed messages.
- Use hardware-based authentication tied to biometric binding for sensitive administrative actions.
- Establish pre-shared secret phrases or one-time verification tokens for high-risk requests, and never accept identity claims solely based on live video or audio.
- Deploy behavior-based anomaly detection that establishes normal transaction and communication patterns to identify deviations quickly.
Tip 4: Keep your crypto holdings private and physically secure
Physical coercion attacks—often called wrench attacks—rose in 2025, with dozens of incidents recorded where attackers physically threatened holders to obtain keys. While still rare, these events highlight that operational security must extend beyond digital precautions.
An X user under the handle Beau, a former CIA officer, said in an X post on Dec. 2 that wrench attacks are still relatively rare, but he still recommends crypto users take precautions by not talking about wealth or disclosing crypto holdings or extravagant lifestyles online as a start.
Physical OPSEC and privacy measures
- Avoid publicly disclosing holdings, addresses, or luxury purchases linked to your identity.
- Use data-cleanup tools to remove or hide personal information tied to public records.
- Invest in home security—cameras, alarms, and secure storage for backup seed material.
- Consider geographic and social compartmentalization: separate the people who know sensitive details from your public-facing profiles.
Tip 5: Reinforce tried-and-true security fundamentals
Despite rapidly evolving threats, many effective defenses remain foundational and straightforward. Security veterans recommend sticking with reputable service providers that undergo regular third-party audits and demonstrate robust security across smart contracts, infrastructure, and operational practices.
Core user-level protections
- Never reuse passwords across accounts; use a password manager to generate and store unique credentials.
- Enable hardware-based multi-factor authentication (MFA) and prefer hardware tokens for exchanges and admin accounts.
- Protect seed phrases by encrypting backups or storing them offline in secure physical locations; never disclose them online.
- Keep large holdings in dedicated hardware wallets and minimize balance on custodial exchanges.
When connecting a hardware wallet to web applications, always verify transaction details on the device screen to avoid blind signing malicious contracts. Treat unsolicited links, files, or download requests as potential attack vectors and verify through independent channels before responding.
Operational security for teams: audits, drills, and segregation
For organizations, the recommended posture includes regular security audits, strict separation of development and production environments, and rehearsed incident response playbooks. Simulated phishing and social-engineering tests should be routine to maintain awareness and measure organizational readiness.
Generate cryptographic keys using secure random number generators, rotate signing keys regularly, and enforce the principle of least privilege across all systems. Combining these practices with automated anomaly detection and human training reduces the chance that a convincing scam will succeed.
Conclusion: Radical skepticism and continuous vigilance
As AI and automation increase the reach and realism of social-engineering attacks, the weakest link in crypto security remains human trust. Adopt a posture of radical skepticism: verify identity, authenticate requests through multiple channels, and assume every unexpected interaction could be a test. No legitimate service will ask for your seed phrase or primary login credentials—when that happens, you are dealing with a scammer.
By combining automation, infrastructure segregation, proof-of-personhood techniques, strong physical and operational security, and basic hygiene like hardware wallets and unique passwords, individuals and organizations can significantly reduce their exposure to social-engineering thefts in 2026 and beyond.
Source: cointelegraph
Comments
Tomas
Ive seen targeted social hacks at a startup i worked at, attackers are crafty. Hardware wallets helped but ppl still fall for convo scams. Train the team.
atomwave
Is this even true? AI deepfakes on Zoom, wrench attacks, and $3.4B lost? feels wild, but how much is double counting, or sensationalized.. curious


Leave a Comment